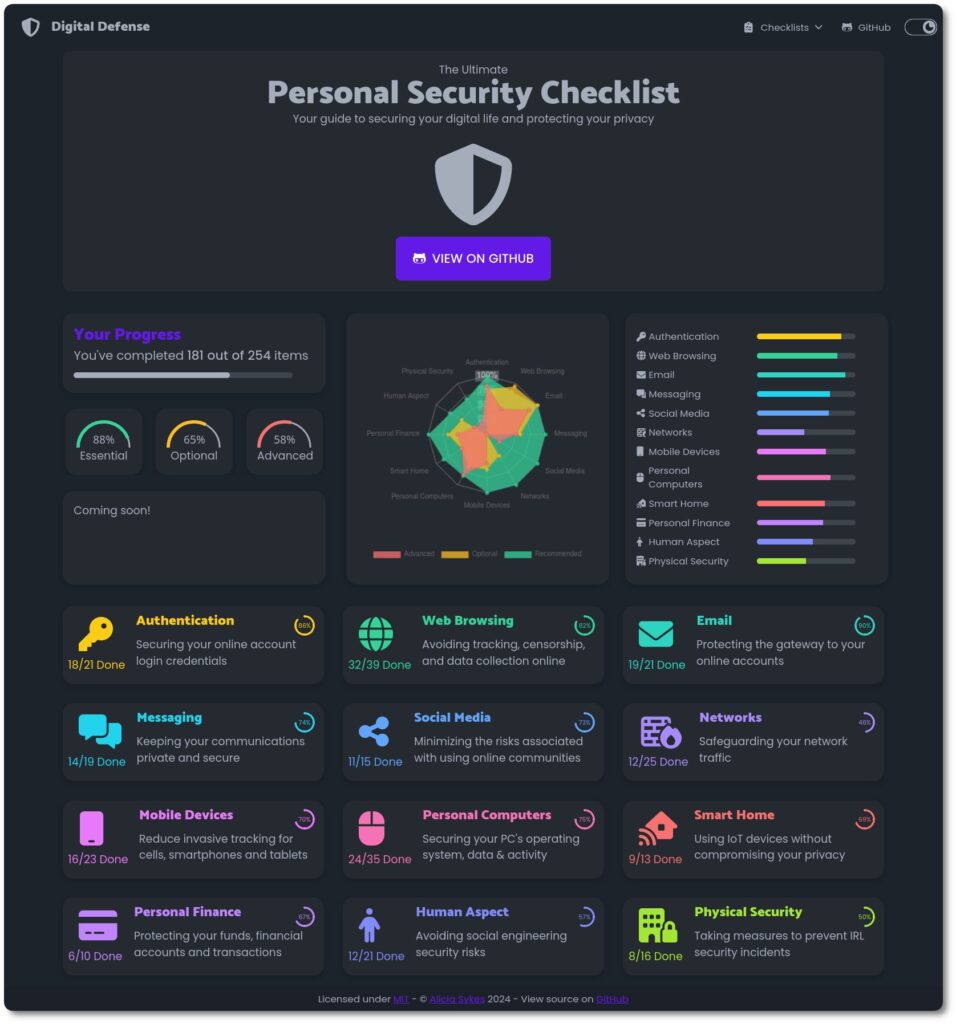
Authentication
Weak, default or stolen passwords cause most reported data breaches. Use long, strong and unique passwords. Manage them in a secure password manager. Activate 2-factor authentication. Keep on top of breaches. Be careful while logging into your accounts.
- Use a strong password
- Don’t reuse passwords
- Use a secure Password Manager
- Enable 2-Factor Authentication
- Keep backup codes safe
- Shield your password/PIN
- Don’t save your passwords in browsers
- watch out for keyloggers
Web Browser
Most websites on the internet will use some form of tracking, often to gain insight into their users behaviour and preferences. This data can be incredibly detailed, and so is extremely valuable to corporations, governments and intellectual property thieves. Data breaches and leaks are common, and deanonymizing users web activity is often a trivial task.
There are two primary methods of tracking; stateful (cookie-based), and stateless (fingerprint-based). Cookies are small pieces of information, stored in your browser with a unique ID that is used to identify you. Browser fingerprinting is a highly accurate way to identify and track users wherever they go online. The information collected is quite comprehensive, and often includes browser details, OS, screen resolution, supported fonts, plugins, time zone, language and font preferences, and even hardware configurations.
- Block ads
- Use a privacy respecting browser
- Use a private search engine
- Remove unnecessary browser Addons
- Keep browser up-to-date
- Check for HTTPS
- Use DNS-over-HTTPS
- Use incognito
- Understand your browser fingerprint
- Manage Cookies
- Block third party trackers
The first email was sent nearly 50 years ago. It’s still very much a big part of our day-to-day life. It will continue to be for the near future. So considering how much trust we put in them, it’s surprising how fundamentally insecure this infrastructure is. Email-related fraud is on the up, and without taking basic measures you can be at risk.
If a hacker gets access to your emails, it provides a gateway for your other accounts to be compromised. This can happen through password resets. Therefore, email security is paramount for your digital safety.
The big companies providing “free” email service, don’t have a good reputation for respecting user’s privacy. Gmail was caught giving third party full access to user emails. It was also caught tracking all your purchases. Yahoo was also caught scanning emails in real time for US surveillance agencies. Advertisers were granted access to Yahoo and AOL users’ messages. They can identify and segment potential customers by picking up on contextual buying signals and past purchases.
- Have more than one email address
- Keep email address private
- Keep your account secure
- Disable automatic loading of remote content
- Don’t share private or sensitive data via email
- Consider switching to a secure email provider
Messaging
- Only use fully end-to-end encrypted messengers
- Use a trustworthy Messaging Platform
- Check security settings
- Disable cloud services
- Secure group chats
- Strip Meta-data from media
- Defang URLs
Social Media
Online communities have existed since the invention of the internet. They give people around the world the opportunity to connect, communicate, and share. Although these networks are a great way to promote social interaction and bring people together, they have a dark side. There are some serious Privacy Concerns with Social Networking Services. These social networking sites are owned by private corporations. They make their money by collecting data about individuals and selling that data, often to third-party advertisers.
Secure your account. Lock down your privacy settings. However, be aware that all data, whether intentionally or non-intentionally uploaded, is effectively public. If possible, avoid using conventional social media networks.
- Secure your account
- Check privacy settings
- Think of all interactions as public
- Think of all interactions as permanent
- Don’t reveal too much
- Don’t share your email or phone number
- Don’t grant unnecessary permissions
- Be careful with 3rd-party integration’s
- Avoid publishing geo data
- Remove metadata before uploading media
Networks
- Use a VPN
- Change your router password
- Use a WPA2, and a strong password
- Keep router firmware up-to-date
- Protect against DNS leaks
- Disable WPS
- Use a Guest network for guests
- Don’t have unnecessary open ports
- Whitelist MAC addresses
Mobile Devices
Smart phones have revolutionized so many aspects of life and brought the world to our fingertips. For many of us, smart phones are our primary means of communication, entertainment and access to knowledge. But while they’ve brought convenience to whole new level, there’s some ugly things going on behind the screen. Geo-tracking traces our every move. We have little control over who has this data. Your phone can even track your location without GPS.
Over the years, numerous reports have surfaced. These reports outline ways in which your phone’s mic can eavesdrop. The camera can watch you—all without your knowledge or consent. And then there’s the malicious apps, lack of security patches and potential/ likely backdoor. Using a smart phone generates a lot of data about you. This includes information you intentionally share. It also includes data silently generated from your actions. It can be scary to see what Google, Microsoft, Apple and Facebook know about us. Sometimes they know more than our closest family.
It’s hard to comprehend what your data will reveal, especially in conjunction with other data. This data is used for far more than just advertising. More often, it rates people for finance, insurance, and employment. Targeted ads can even be used for fine-grained surveillance.
More of us are concerned about how governments collect and use our smartphone data. And rightly so. Federal agencies often request our data from Google, Facebook, Apple, Microsoft, Amazon, and other tech companies. Sometimes requests are made in bulk, returning detailed information on everybody within a certain geo-fence, often for innocent people. And this doesn’t include all of the internet traffic that intelligence agencies around the world have unhindered access to.
- Encrypt your device
- Turn off connectivity features that aren’t being used
- Keep app count to a minimum
- Check app permitions
- Only install apps from the official store
- Be careful of phone charging threats
- Set up a mobile carrier PIN
- Use Offline Maps
- Monitor trackers
- Restart or device regularly
Personal Computers
Although Windows and OS X are easy to use and convenient, they both are far from secure. Your OS provides the interface between hardware and your applications, so if compromised can have detrimental effects.
- Keep your system up-to-date
- Encrypt your device
- Back up important data
- Be careful when plugging in USB devices
- Activate screen-lock when idle
- Disable Cortana or Siri
- Review your installed apps
- Manage permissions
- Don’t use Root/Admin account non admin tasks
- Block webcam and microphone
- Use a firewall
- Make use of VMs
- Protect against software keyloggers
Smart Home
Home assistants, like Google Home, Alexa, and Siri, collect extensive personal data. This includes voice samples, location data, home details, and logs of all interactions. You have limited control over what is being collected. You also cannot fully control how it’s stored or what it will be used for. Consequently, it is hard to recommend any consumer smart-home products to anyone who cares about privacy and security.
Security vs Privacy: Many smart devices are on the market. They claim to enhance your home’s security. These devices are easy and convenient to use. Examples include Smart Burglar Alarms, Internet Security Cameras, Smart Locks, and Remote Access Doorbells.
These devices may appear to make security easier. However, there is a trade-off in terms of privacy. They collect large amounts of personal data. You lose control over how this is stored or used. The security of these devices is also questionable. Many of them can be hacked. Intruders bypass detection with minimum effort.
The most privacy-respecting option is to avoid using “smart” internet-connected devices in your home. Do not rely on a security device that requires an internet connection. But if you do, it is important to fully understand the risks of any given product, before buying it. Then adjust settings to increase privacy and security. The following checklist will help mitigate the risks associated with internet-connected home devices.










