Dynamic Duo: Snort and Wireshark
In the dynamic landscape of cybersecurity, where threats are constantly evolving and becoming more sophisticated, the need for powerful tools to analyze network traffic has never been more critical. Two stalwarts in the arsenal of cybersecurity analysts, Snort and Wireshark, play a pivotal role in unravelling the mysteries hidden within the vast expanse of data flowing through networks. In this blog post, I’ll explore the importance of these tools and how they empower cybersecurity analysts to enhance their ability to detect and mitigate cyber threats.
Unveiling Threats with Snort:
1. Intrusion Detection and Prevention: Snort, an open-source intrusion detection and prevention system, acts as the first line of defence against cyber threats. It analyzes network traffic in real time, using predefined rules to detect and alert suspicious activities. By actively monitoring for known attack patterns, Snort enables cybersecurity analysts to identify and respond to potential threats swiftly.
2. Signature-Based Detection: Snort employs signature-based detection to identify patterns associated with known threats. This approach allows for the rapid identification of malicious activities, making it an invaluable tool for cybersecurity analysts tasked with safeguarding network integrity.
3. Flexible and Customizable: One of Snort’s strengths lies in its flexibility and customization options. Analysts can tailor the rules to suit the specific needs of their network, ensuring that the system is finely tuned to detect threats relevant to their environment.
Wireshark: The Visual Gateway to Network Analysis:
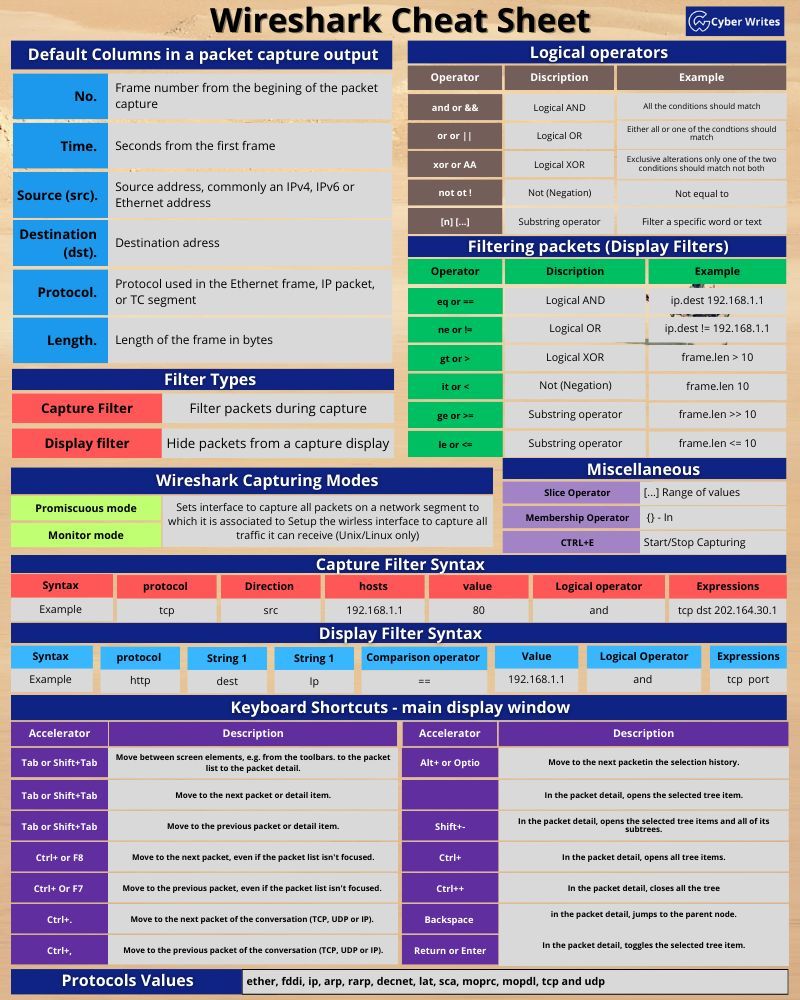
1. Graphical Network Protocol Analyzer: Wireshark, a graphical network protocol analyzer, complements Snort by providing a visual representation of network traffic. Its intuitive interface allows cybersecurity analysts to dissect and analyze packets at a granular level, revealing the inner workings of communication on the network.
2. Deep Packet Inspection: Wireshark’s deep packet inspection capabilities are instrumental in understanding the intricacies of network communication. Analysts can explore protocol headers, examine payloads, and identify anomalies that may indicate security threats.
3. Collaboration and Reporting: Wireshark facilitates collaboration among cybersecurity professionals. Its ability to save and share captures allows teams to work collectively on analyzing network traffic, improving incident response, and enhancing overall cybersecurity resilience.
Conclusion:
In the ever-evolving landscape of cybersecurity, the collaboration between Snort and Wireshark emerges as a force multiplier. By leveraging Snort’s real-time threat detection capabilities and Wireshark’s detailed packet analysis, cybersecurity analysts can fortify their defences, respond effectively to incidents, and stay one step ahead of cyber adversaries. As the digital frontier continues to expand, this dynamic duo remains a cornerstone in the quest to secure networks and uphold the resilience of our interconnected world.
For your laptop or any other device needs, please click on the following link. Thank you.
Next article: Mitre Attack Framework










